Heartbleed Command for Splunk
 Discovered Intelligence has developed a simple Splunk command for identifying Heartbleed vulnerabilities!
Discovered Intelligence has developed a simple Splunk command for identifying Heartbleed vulnerabilities!
This CIM-Compliant Technology Add-on (TA-Heartbleed) contains a new heartbleedtest Splunk command that can be used to check your internal infrastructure and external websites for the recently announced Heartbleed vulnerability.
Upon invoking the command on your Splunk search results, it will run a check against provided host/port values and return a new field, named vulnerable, that will state whether the host values are vulnerable to heartbleed or not.
How to use the command
The command is invoked as follows:
| heartbleedtest serverfield=[serverfield] portfield=[portfield] timeout=[int] poolsize=[int]
Note: fieldvalue, port, timeout and poolsize are optional. Here are the defaults when they are not specified:
serverfield = dest
portfield = port
timeout = 3
poolsize = 10
- The serverfield field contains host values (e.g. google.com, yahoo.com, myserver.company.com)
- The portfield contains port numbers (e.g. 443, 8000)
- Timeout is declared as an integer
- Poolsize is declared as an integer and represents how many concurrent threads are launched with the command. For example, the default poolsize of 10 will allow for 10 hosts to be checked by the command at once, whereas a poolsize of 100 will allow 100 hosts to be checked at once.
NOTE: Use caution with the poolsize. The greater the poolsize, the more memory is used. A poolsize of 100 seems to be a nice sweetspot, but if you go higher, please use caution.
Example searches
MySplunkSearch | heartbleedtest serverfield=dest portfield=port timeout=3 poolsize=10 | table dest port vulnerable
These are actually the default variables and we do not actually need to declare them – we are doing so here for illustrative purposes. This will run the heartbleed test on using the default serverfield of dest, the default portfield of port, the default timeout of 3 seconds and the default poolsize of 10. It will tabulate the results and tell you if any dest values are vulnerable.
MySplunkSearch | heartbleedtest serverfield=myHostField portfield=myPortField timeout=10 poolsize=100 | table myHostField myPortField vulnerable
This will run the heartbleed test on a serverfield of myHostField, a portfield of myPortField, a timeout of 10 seconds and a poolsize of 100. It will tabulate the results and tell you if any myHostField values are vulnerable.
Installation
To install the command – download the TA here, then install into Splunk as you would do any other app and you should be all set. The command is set to be global, so should work from any of your existing apps. The command should be in the Splunk App store very shortly.
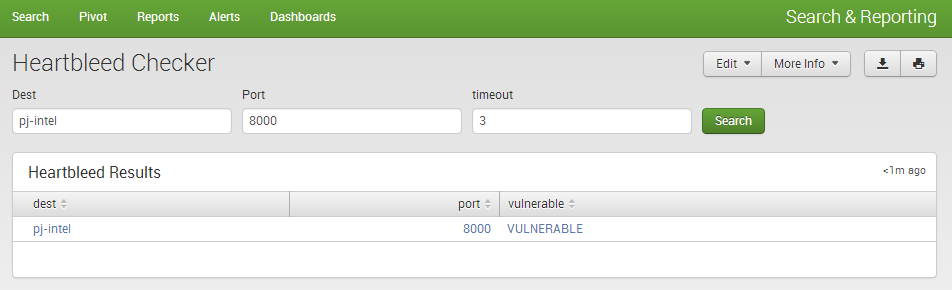
An Example Dashboard
We have knocked up a quick Heartbleed Checker dashboard form that allows you to leverage the command on a nice form in Splunk to check hosts/ports individually and get the results back. You should just be able to copy and paste into an empty view/dashboard. Feel free to edit where you see fit.
<form>
<label>Heartbleed Checker</label>
<fieldset autoRun=”false” submitButton=”true”>
<input type=”text” token=”dest”>
<label>Dest</label>
</input>
<input type=”text” token=”port”>
<label>Port</label>
<default>443</default>
</input>
<input type=”text” token=”timeout”>
<label>timeout</label>
<default>3</default>
</input>
</fieldset>
<row>
<table>
<title>Heartbleed Results</title>
<searchString>index=_* earliest=-60m | head 1 | eval port=”$port$” | eval timeout=”$timeout$” | eval dest=”$dest$” | heartbleedtest | table dest port vulnerable</searchString>
</table>
</row>
</form>
For support, feedback, questions, concerns – feel free to contact us: support<AT>discoveredintelligence.ca
Looking to expedite your success with Splunk? Click here to view our Splunk service offerings.
© Discovered Intelligence Inc., 2014. Do More with your Big Data™. Unauthorised use and/or duplication of this material without express and written permission from this site’s owner is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to Discovered Intelligence, with appropriate and specific direction (i.e. a linked URL) to this original content.